A security administrator is trying to determine whether a server is vulnerable to a range of attacks. After using a tool, the administrator obtains the following output:
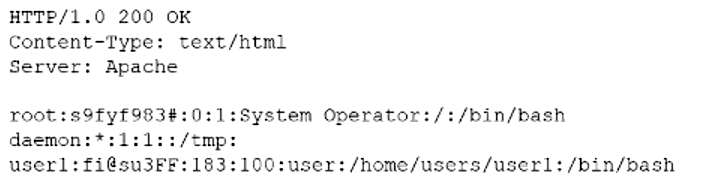
Which of the following attacks was successfully implemented based on the output?
A. Memory leak
B. Race conditions
C. SQL injection
D. Directory traversal

Which of the following attacks was successfully implemented based on the output?
A. Memory leak
B. Race conditions
C. SQL injection
D. Directory traversal