A security analyst needs to determine how an attacker was able to use User3 to gain a foothold within a company's network. The company's lockout policy requires that an account be locked out for a minimum of 15 minutes after three unsuccessful attempts. While reviewing the log files, the analyst discovers the following:
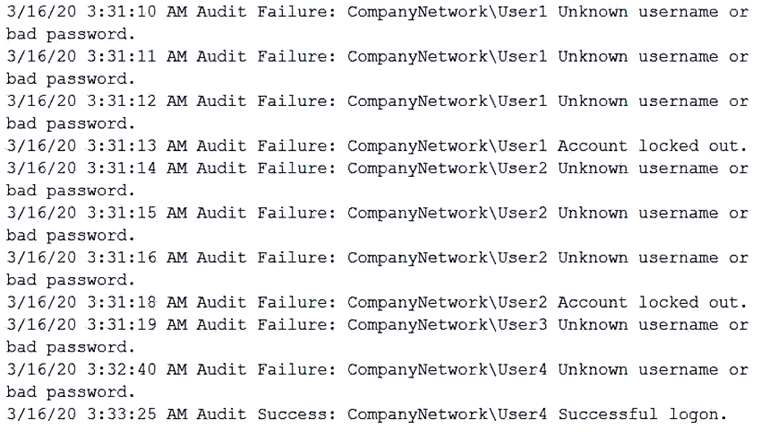
Which of the following attacks MOST likely occurred?
A. Dictionary
B. Credential-stuffing
C. Password-spraying
D. Brute-force

Which of the following attacks MOST likely occurred?
A. Dictionary
B. Credential-stuffing
C. Password-spraying
D. Brute-force