During an incident response, a security analyst observes the following log entry on the web server:
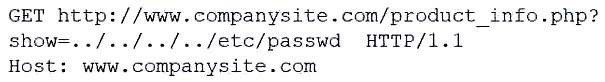
Which of the following BEST describes the type of attack the analyst is experiencing?
A. SQL injection
B. Cross-site scripting
C. Pass-the-hash
D. Directory traversal