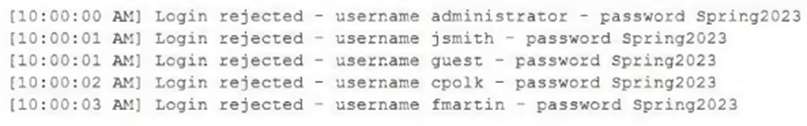
A security analyst discovers that one of the web APIs is being abused by an unknown third party. Logs indicate that the third party is attempting to manipulate the parameters being passed to the API endpoint. Which of the following solutions would best help to protect against the attack?
A. DLP
B. SIEM
C. NIDS
D. WAF
A. DLP
B. SIEM
C. NIDS
D. WAF