A network engineer receives a call regarding multiple LAN-connected devices that are on the same switch. The devices have suddenly been experiencing speed and latency issues while connecting to network resources.
The engineer enters the command show mac address-table and reviews the following output:
The engineer enters the command show mac address-table and reviews the following output:
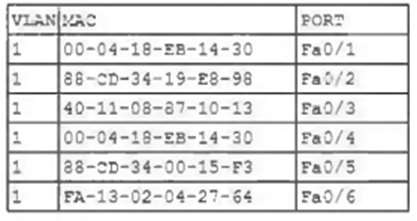
Which of the following best describes the attack that is currently in progress'?
A. MAC flooding
B. Evil twin
C. ARP poisoning
D. DHCP spoofing