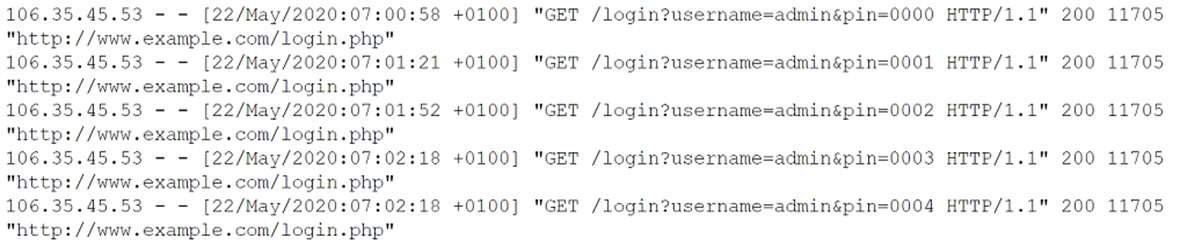
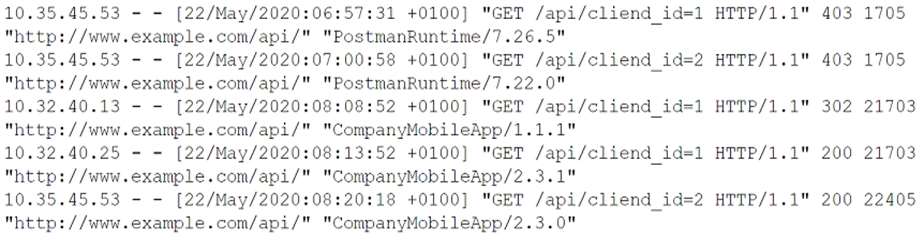
A company recently enhanced mobile device configuration by implementing a set of security controls biometrics
context-aware authentication and full device encryption. Even with these settings in place, an unattended phone
was used by a malicious actor to access corporate data. Which of the following additional controls should be
put in place first?
A. GPS tagging
B. Remote wipe
C. Screen lock timer
D. SEAndroid
context-aware authentication and full device encryption. Even with these settings in place, an unattended phone
was used by a malicious actor to access corporate data. Which of the following additional controls should be
put in place first?
A. GPS tagging
B. Remote wipe
C. Screen lock timer
D. SEAndroid