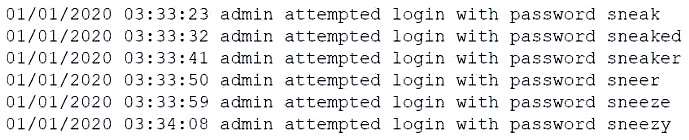
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible
Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Choose two.)
A. MAC filtering
B. Zero trust segmentation
C. Network access control
D. Access control vestibules
E. Guards
F. Bollards
Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Choose two.)
A. MAC filtering
B. Zero trust segmentation
C. Network access control
D. Access control vestibules
E. Guards
F. Bollards