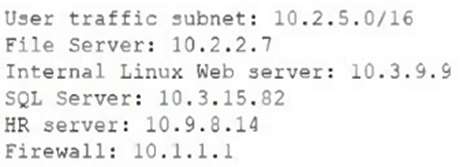
A recent vulnerability scan revealed multiple servers have non-standard ports open for applications that are no longer in use. The security team is working to ensure all devices are patched and hardened. Which of the following would the security team perform to ensure the task is completed with minimal impact to production?
A. Enable HIDS on all servers and endpoints.
B. Disable unnecessary services.
C. Configure the deny list appropriately on the NGFW.
D. Ensure the antivirus is up to date.
A. Enable HIDS on all servers and endpoints.
B. Disable unnecessary services.
C. Configure the deny list appropriately on the NGFW.
D. Ensure the antivirus is up to date.