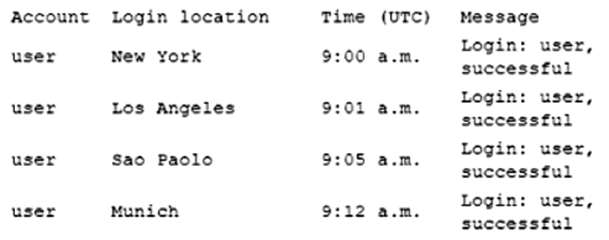
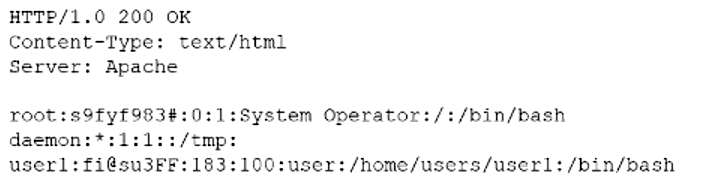
An organization is tuning SIEM rules based off of threat intelligence reports. Which of the following phases of
the incident response process does this scenario represent?
A. Lessons learned
B. Eradication
C. Recovery
D. Preparation
the incident response process does this scenario represent?
A. Lessons learned
B. Eradication
C. Recovery
D. Preparation