A security analyst is reviewing web-application logs and finds the following log:
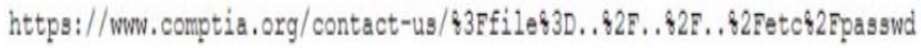
Which of the following attacks is being observed?
A. Directory traversal
B. XSS
C. CSRF
D. On-path attack
Which of the following attacks is being observed?
A. Directory traversal
B. XSS
C. CSRF
D. On-path attack