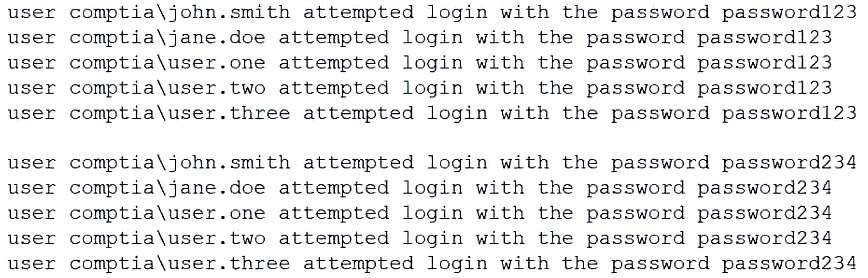
A manufacturing organization wants to control and monitor access from the internal business network to the segregated production network, while ensuring minimal exposure of the production network to devices. Which of the following solutions would best accomplish this goal?
A. Proxy server
B. NGFW
C. WAF
D. Jump server
A. Proxy server
B. NGFW
C. WAF
D. Jump server