A security analyst is reviewing the following command-line output:
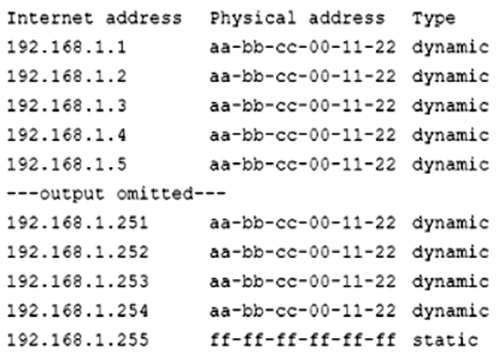
Which of the following is the analyst observing?
A. ICMP spoofing
B. URL redirection
C. MAC address cloning
D. DNS poisoning

Which of the following is the analyst observing?
A. ICMP spoofing
B. URL redirection
C. MAC address cloning
D. DNS poisoning