A security analyst is investigating what appears to be unauthorized access to a corporate web application. The security analyst reviews the web server logs and finds the flowing entries:
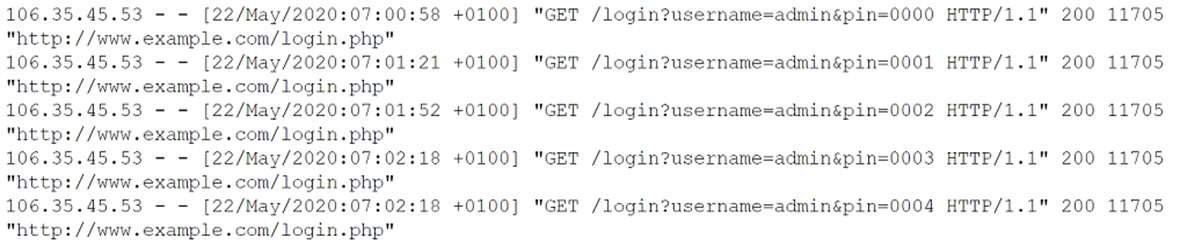
Which of the following password attacks is taking place?
A. Dictionary
B. Brute-force
C. Rainbow table
D. Spraying